Penetration testing services
What you'll get after conducting a pentest project:
- Executive summary outlining risk management implications
- Technical report detailing identified vulnerabilities
- Step-by-step recommendations for fixing identified vulnerabilities
- Expert guidance on cybersecurity improvement strategies
- Attestation to meet compliance requirements
What's a Penetration Test?
Penetration Testing, commonly referred to as ‘pen testing’ or ethical hacking, is a crucial cybersecurity analysis that proactively identifies and helps to fix vulnerabilities in an organization’s computer systems, networks, applications or smart devices. The assessment involves simulating controlled hacking techniques, mirroring strategies employed by real-world attackers to test the resilience of the target and its defenses against security breaches.
It helps organizations understand precisely what could be achieved if they were targeted by a real cyberattack and how to prevent potential impacts. It’s instrumental in helping organizations enhance their security posture. Through penetration testing, businesses gain a realistic assessment of their preparedness against cyber threats and ensure compliance with various regulatory standards, helping stakeholders prioritize their most critical risks and make informed decisions to safeguard their digital assets.
In a landscape where cyber threats are constantly evolving, conducting regular penetration testing is essential to ensure that security measures are both robust and adapted to the latest adversary tactics. Various standards, such as PCI-DSS or ISO27001 mandate yearly testing to maintain compliance and avoid costly fines in the event of an incident.
Why Should you Perform Penetration Testing?
- Evolving security landscape
Adapting to rapidly evolving security threats and hacking techniques employed against critical IT systems and applications. - Rising complexity of modern security risks
Discovering and addressing often critical security risks that automated tools are unable to identify due to their unique nature. - Increasing cybersecurity requirements
Compliance standards are increasing across all industries and now include recurring penetration testing as a requirement. - Limitations in traditional security solutions
Conventional security tools, like firewalls and antivirus software are generally ineffective, lacking comprehensive coverage against a broader range of vulnerabilities.

How Will Penetration Testing Help Improve My Cybersecurity?
- Gain In-Depth Insight Into Current Risks
Conduct an in-depth external penetration test that transcends basic automated scanning tools to offer a comprehensive security assessment of your external network. - Simulate Real-World External Threats
Replicate hacking techniques and exploits, such as unauthorized access and software exploitation, to pinpoint your most vulnerable assets. - Benchmark Against Industry Standards
Measure your external security posture against globally recognized security frameworks to gauge how well you’re doing in the larger landscape. - Adopt the Latest Best Practices
Deploy robust security mechanisms to fortify your target systems against a spectrum of threats, both conventional and emergent, thereby minimizing the attack surface.
What Can be Assessed by Penetration Testing?
A pentest can be used to identify & fix vulnerabilities across various kinds of digital technologies used by organizations today:
- Network Infrastructure
In-depth analysis of internal and external networks. Firewalls, IDS/IPS systems, VPN configurations, network device settings, etc. - Application Security
Assessment of Web / mobile applications and APIs against OWASP top 10 vulnerabilities, business logic flaws, etc. - Cloud Infrastructure
Review of cloud-hosted assets across various platforms (AWS, Azure, Google), and their specific components/configurations. - Smart Devices
Security testing of medical devices, consumer products, commercial IoT devices and their specific features/protocols. - Industrial SCADA / ICS
Audit of SCADA software / hardware components or ICS network protocols, remote access, segmentation, etc. - And More
Including phishing simulation to assess employee awareness, red & purple teaming to improve incident prevention capabilities, etc.
Why Conduct a Penetration Test?
Enhanced Security Posture
Implement effective security measures to protect your organization from a wide range of cyber threats and gain an improved security posture.
Achieved Compliance
Successfully meet various types of regulatory requirements, such as insurance requests, SOC 2, PCI, ISO 27001, FDA, HIPAA, etc.
Prioritized Security Investments
Get a prioritized list of cybersecurity improvements to focus your resources on your most critical risks of facing an incident.
Protected Business Continuity
Strengthens the organization's resilience against disruptions, ensuring availability of services / operations and limiting the potential impact of an attack.
Strengthened Customer Trust
By mitigating potential attack vectors, penetration testing minimizes the risk of data breaches, a key factor in maintaining customer trust.
Improved Risk Visibility
Presents an independent perspective of your current security posture to help IT teams demonstrate risk to executives and non-technical stakeholders effectively.
Network Penetration Testing
External Network Penetration Testing
Our external pentest services identify vulnerabilities in your organization’s public-facing infrastructure to determine if an external attacker can breach your perimeter. Protect your digital assets and ensure your organization’s defenses are effective against the most common type of cyber threats.
Internal Network Penetration Testing
Our internal pentest services evaluate the security of your organization’s internal infrastructure, identifying vulnerabilities and potential attack vectors from insider threats or external attackers who have gained access. Strengthen your defenses against these threats, safeguard critical data, and ensure a robust cybersecurity posture within your internal network.
Wireless Network Penetration Testing
Our Wireless Network Penetration Testing service provides a comprehensive assessment of your wireless network infrastructure to identify vulnerabilities that may be exploited by hackers. We use top industry standards and common hacking techniques to simulate real-world attacks and provide valuable insights into the security posture of your wireless network.
Mainframe Penetration Testing
Our Mainframe Penetration Testing services evaluate the security of your mission-critical mainframe systems by identifying and addressing vulnerabilities that could be exploited by hackers. Safeguard your organization’s valuable data, maintain compliance with industry regulations, and strengthen your overall security posture by proactively addressing mainframe-specific risks.
Industrial SCADA Penetration Testing
Our SCADA penetration testing services evaluate the security of your industrial control systems and critical infrastructure, identifying vulnerabilities that could be exploited by malicious attackers. Safeguard your automated processes and critical systems from targeted attacks, ensuring the resilience of your SCADA environment against ever-evolving cyber threats.


Application Penetration Testing
Vumetric is an industry leader in the field of application security testing. Our methodology combines manual tests and automated tools to identify the most complex business logic flaws. Based on the OWASP Top 10 and over 15 years of experience in the industry.
Web Application Penetration Testing
Our Web Application Penetration Testing services uncover vulnerabilities in your web applications, assessing their security posture against potential cyberattacks. Safeguard your sensitive data and maintain the trust of your users by ensuring your web applications are protected against the most prevalent and sophisticated threats in the digital landscape.
Mobile Application Penetration Testing
Our Mobile App Penetration Testing services evaluate the security of your mobile applications (iOS & Android), identifying potential vulnerabilities and ensuring robust protection against cyber attacks. Safeguard your users’ sensitive data and maintain compliance with industry standards while delivering a secure and trustworthy mobile experience.
API Penetration Testing
Our API Security Testing services evaluate the security posture of your APIs to identify vulnerabilities and potential attack vectors. Safeguard your data and ensure your API infrastructure is resilient against both common and advanced cybersecurity threats, maintaining the integrity and availability of your digital services.
Thick Client Penetration Testing
Our Thick Client Application Security Testing services identify and assess vulnerabilities in your organization’s locally installed software, ensuring robust security against potential attacks. Safeguard your intellectual property, sensitive data, and client-side systems by comprehensively evaluating both local and server-side components, as well as network communications, to enhance your overall cybersecurity posture.
Source Code Review
Our Secure Code Review Services are designed to identify potential security vulnerabilities in the source code of your applications. Our team of security experts will conduct a thorough review of your code, using a combination of manual examination and automated tools to identify any potential security flaws.
Benchmark Your Security Against The Leading Standards

OWASP
Open Web Application Security Project
The OWASP standard is the industry-leading standard for application security, web and mobile alike. This open-source methodology helps organizations around the world strengthen their application security posture by developing, publishing and promoting security standards. We leverage this standard as a baseline for our security testing methodology in order to identify vulnerabilities unique to each application, beyond the capability of automated tools.

MITRE
MITRE ATT&CK FRAMEWORK
The MITRE ATT&CK Framework is a publicly-available knowledge base of techniques and exploits commonly used by real-world hacking groups to breach various technologies used by organizations. Our pentest services are based on this framework in order to measure your cybersecurity risks against known adversary tactics, helping you develop more targeted countermeasures against the current threat landscape and prioritize security improvements efficiently.
Cloud Penetration Testing
With the recent transition to cloud computing technologies, organizations face a new set of unknown security risks. Our cloud penetration testing services are designed to secure any cloud-hosted asset, no matter the cloud provider.
Amazon Web Services (AWS) Penetration Testing
Our Microsoft 365 Security Assessment services evaluate your organization’s cloud environment to uncover potential security risks and compliance issues. Safeguard your sensitive data, enhance access controls, and optimize configurations to ensure your Microsoft 365 ecosystem is resilient against cyber threats and aligned with industry best practices.
Microsoft Azure Penetration Testing
Our Azure Penetration Testing services help organizations validate the security of their assets hosted on Microsoft Azure, and identify and fix technical vulnerabilities that may compromise the confidentiality and integrity of their resources. The assessment can also evaluate the security of the Azure infrastructure hosting the application, and help organizations improve their overall security posture.
Microsoft Office 365 Security Audit
Our Microsoft 365 Security Assessment services evaluate your organization’s cloud environment to uncover potential security risks and compliance issues. Safeguard your sensitive data, enhance access controls, and optimize configurations to ensure your Microsoft 365 ecosystem is resilient against cyber threats and aligned with industry best practices.
Google Cloud Platform Penetration Testing
GCP penetration testing services identify vulnerabilities and assess the security of your applications and infrastructure hosted on Google Cloud Platform. Ensure the protection of your valuable digital assets and verify the effectiveness of your security measures in compliance with Google’s guidelines, while safeguarding your organization against potential cyber threats targeting GCP services.

Got an Upcoming Project? Need Pricing For Your Penetration Test?
Answer a few questions regarding your cybersecurity needs and objectives to quickly receive a tailored quote. No engagement.
- You can also call us directly: 1-877-805-7475
Our Penetration Testing Process
Here’s a high-level overview of each stage in our proven penetration testing process. We keep you informed at every step of the project.
Project Scoping
Duration: ~ 1-2 days
Activities: We learn about your specific needs and objectives.
Outcome: Business proposal, signed contract.
Kick-off / Planning
Duration: ~ 1 hour
Activities: We review the scope of work, discuss requirements and planning.
Outcome: Scope validation, test planning.
Penetration Testing
Duration: ~ 2-3 weeks
Activities: We execute the test in accordance with the project scope.
Outcome: Detailed penetration test report, presentation.
Remediation Testing
Duration: Up to 1 month
Activities: We test and validate vulnerability fixes.
Outcome: Remediation report, attestation.
“ More than half of organizations (54%) performed a penetration test in 2022 ”

Adversary Simulation / Red Team
Simulate persistent hacking scenarios to measure the efficiency and the resilience of IT systems / employees to respond to a targeted attack, improving your prevention and incident response capabilities.
Red Team Assessment
Purple Team Assessment
Our Purple Teaming services combine the expertise of both offensive and defensive security teams to assess your organization’s ability to detect and respond to cyberattacks in real-time. Strengthen your security posture, enhance incident response capabilities, and gain invaluable insights to protect your organization from ever-evolving cyber threats.
Phishing Simulation Test
Our Phishing Simulation Testing services assess your employees’ awareness and response to phishing attacks, helping to identify weaknesses in your organization’s cybersecurity posture. Strengthen your defenses against the most prevalent social engineering threats and ensure your team is prepared to recognize and handle real-world phishing attempts.
PENETRATION TESTING AS-A-SERVICE PLATFORM
The Modern Way to Conduct Pentesting
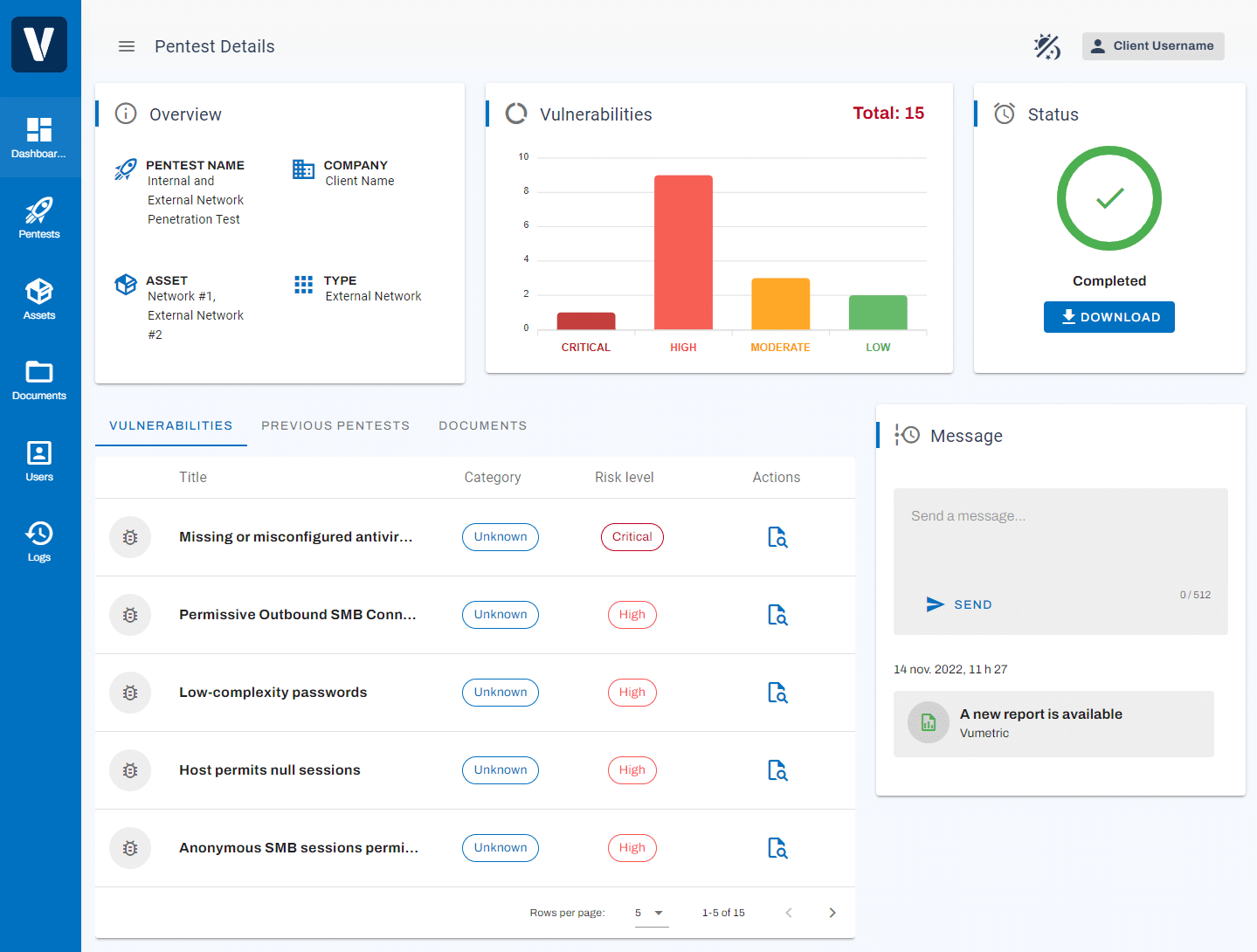
Experienced & Certified Penetration Testing Specialists

OSCP
Offensive Security Certified Professional

OSEP
Offensive Security Experienced Penetration Tester

OSWE
Offensive Security
Web Expert

CRTO
Certified Red Team
Operator

GPEN
GIAC Penetration
Tester

GWAPT
GIAC Web Application Penetration Tester

GXPN
GIAC Exploit Researcher and Advanced Penetration Tester

GSEC
GIAC Security Essentials Certification
The Factors That Determine The Cost of Your Penetration Testing Projects
The cost of a penetration test varies significantly based on a set of factors, making it difficult to provide an accurate price estimate. Projects can range from $5,000 for simple tests to $100,000 for larger multi-phase pentests.
These factors include the type of test conducted, the size of the target environment or the complexity of the application.
To get a better understanding of the potential cost of your pentest, it is essential to schedule a call with a provider to discuss your objectives and scope. This approach ensures that you receive an accurate and customized quote based on your specific requirements so you can better plan budgetary needs for your cybersecurity.
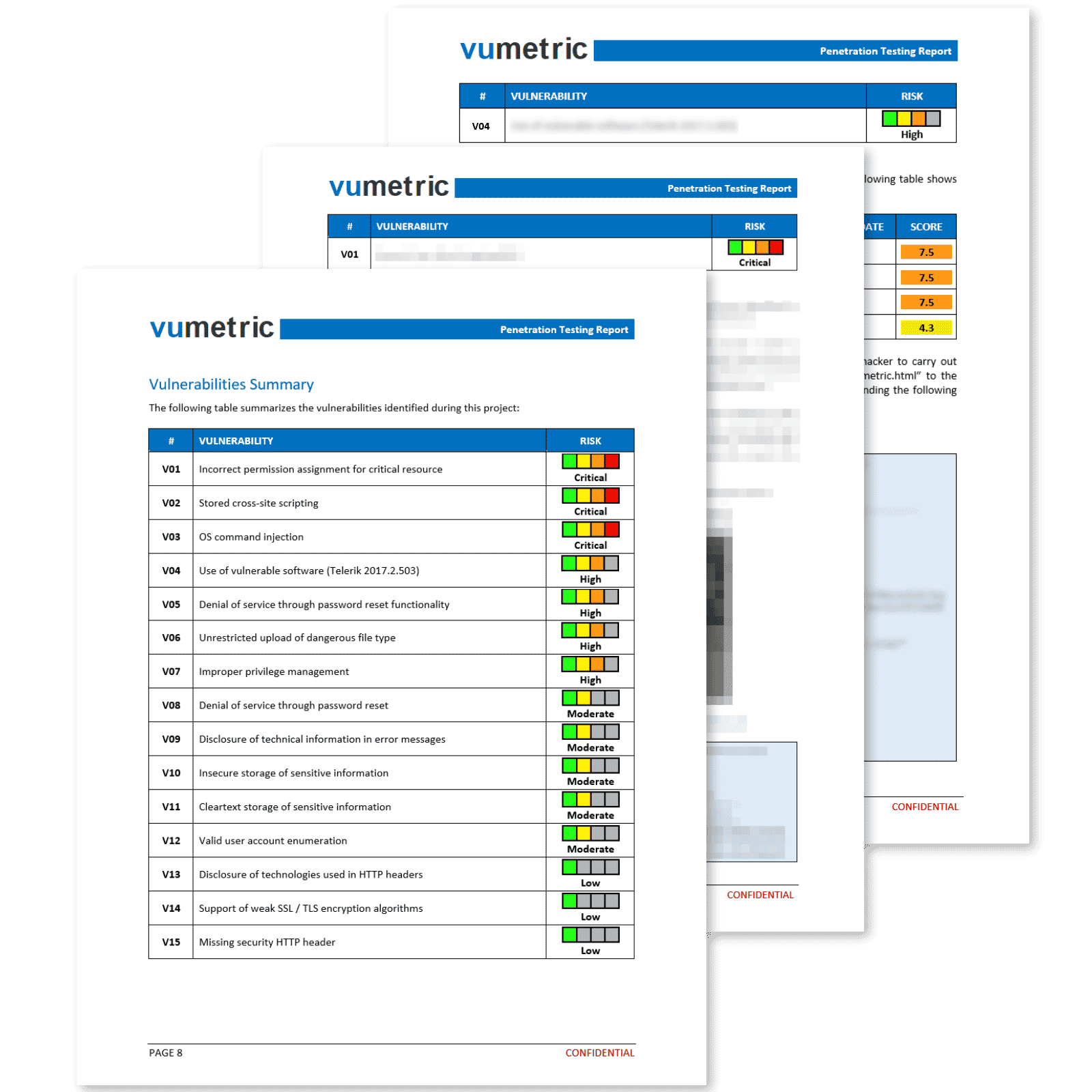
Professional Reporting With Clear & Actionable Results
Our penetration reports deliver more than a simple export from a security tool. Each vulnerability is exploited, measured and documented by an experienced specialist to ensure you fully understand its business impact.
Each element of the report provides concise and relevant information that contributes significantly towards improving your security posture and meeting compliance requirements:
Executive Summary
High level overview of your security posture, recommendations and risk management implications in a clear non-technical language.
Suited for non-technical stakeholders.
Vulnerabilities & Recommendations
Vulnerabilities prioritized by risk level, including technical evidence (screenshots,
requests, etc.) and recommendations to fix each vulnerability.
Suited for your technical team.
Attestation
This document will allow you to meet compliance and regulatory reporting requirements efficiently and with minimal overhead.
Suited for third-parties (clients, auditors, etc).
Penetration Testing FAQ
Couldn’t find the information you were looking for? Ask an expert directly.
Conducting a penetration test is a critical tool used by companies as part of their cybersecurity risk management strategy. It helps organizations identify and fix the vulnerabilities most likely to be exploited to breach their cybersecurity and offers counter-measures to mitigate the most important risks of facing cybersecurity incidents.
The process involves an initial pre-engagement phase to define scope and objectives, followed by reconnaissance, scanning, exploitation, and post-exploitation stages to identify vulnerabilities and assess potential impacts. Detailed reports are provided after testing to help you understand and address discovered issues.
The cost of a penetration test can vary significantly depending on the scope of the assessment. For external penetration testing, one of the most significant factors in the price is the number of IP addresses that need to be evaluated. For an application penetration test, the complexity of the app and the number of user roles will directly impact pricing.
Learn more about the main factors that determine the cost of a penetration test →
Quickly receive a free quote with no engagement using our streamlined quoting tool →
Our penetration tests are designed to minimize disruption to your organization’s normal operations and the overwhelming majority of our tests are unnoticeable to our clients. Our team will work with you prior to the project launch to determine any areas that may be susceptible to affect your productivity and will take the necessary steps to minimize any potential impact.
In most cases, no access or permissions are required for a penetration test. The goal is to replicate an authentic cyber threat attempting to circumvent your security measures therefore the test is conducted entirely without any inside knowledge or access. However, some types of tests may require access is required to achieve the desired outcome. For example, in order to accurately test an industrial system, remote access to the network may be needed. We will coordinate with your team during the project launch call, where we will confirm objectives, the testing target, as well as any access requirements to achieve project goals.
Penetration testing is an essential component of any comprehensive cybersecurity strategy. By identifying vulnerabilities and weaknesses in your mission-critical networks and applications, you can take proactive steps to protect your organization from the most likely risks of facing potential a damaging breach. Regular testing can help ensure that your security measures are up-to-date and effective, and can provide valuable insights into areas that may require additional attention or investment.
Our penetration tests helps several organizations of all types meet compliance requirements every year by identifying vulnerabilities that need remediation. Once remediation testing is completed, we provide an official attestation confirming that vulnerabilities have been remediated, helping organizations meet compliance requirements efficiently.
The duration of the test varies depending on the size and complexity of the scope. A typical pentest project can range from a few days, up to 3 weeks.
Why Choose Vumetric For Penetration Testing?
Vumetric is an ISO9001-certified boutique provider entirely dedicated to pen test, with more than 15 years of experience in the industry. Our methodologies are proven and our understanding of cybersecurity risks is extensive, allowing us to provide clear advice to our clients that is pragmatic, adapted to their needs and efficient in securing against any malicious attacker.
Recognized & Proven
Testing Methodologies
Our testing methodologies are based on industry best practices and standards.
ExperiencedTeam
Our team of certified penetration testers conducts more than 400 pentest projects annually.
Actionable Results
We provide quality reports with actionable recommendations to fix identified vulnerabilities.
Download Our External Penetration Testing Case Study
See our external penetration testing services in action and discover how they can help secure your public-facing network perimeter from modern cyber threats and exploits.
Download Our Medical Device Penetration Testing Case Study
See our medical device penetration testing services in action and discover how they can help secure your smart healthcare equipment and its underlying components from modern threats to achieve FDA compliance.
Download The Vumetric Penetration Testing Buyer's Guide
Learn everything you need to know about penetration testing to conduct successful pentesting projects and make informed decisions in your upcoming cybersecurity assessments.
Download Our Web Application Penetration Testing Case Study
See our Web App penetration testing services in action and discover how they can help secure your mission-critical applications and APIs from modern cyber threats and exploits.
Download Our Internal Penetration Testing Case Study
See our internal penetration testing services in action and discover how they can help secure your internal network infrastructure from modern cyber threats and unauthorized access.
Read Our Clients' Success Stories
Discover how our external pentest services helped organization of all kinds improve their network security:
“ Vumetric conducted external penetration testing and showed us where we were vulnerable. They made the process smooth, were very responsive and well organized. They really impressed us as specialists in their field. ”
Elizabeth W., General Manager
" Vumetric provided external penetration testing services and delivered comprehensive results in a timely manner. They dedicated a highly-skilled, knowledgeable team with excellent customer service. ”
Joe A., IT Infrastrucure Manager
“ Vumetric performed manual and automated security testing of our externally accessible systems. They met our deadlines and kept us updated throughout the testing process. Their presentation of findings and recommendations was engaging and effective. ”
Louis E., Director of IT & CISO
Featured Penetration Testing Resources
Gain insight on emerging hacking trends, recommended best practices and tips to improve your cybersecurity: