Ransomware has become one of the biggest threats to businesses and organizations worldwide in the past few years. This type of malware holds data hostage by encrypting it until ransom money is paid. And as cybercriminals become more sophisticated, the attacks become more frequent and lucrative.
To help you better understand this growing threat, we’ve compiled a list of the 5 biggest ransomware attacks in recent history. While each of these cases offers its own unique set of lessons, there are some key takeaways that all businesses should heed. So, without further ado, let’s look at some of the most devastating ransomware attacks in recent memory.
The 5 devastating Ransomware Attacks
#1 WannaCry Ransomware Attack
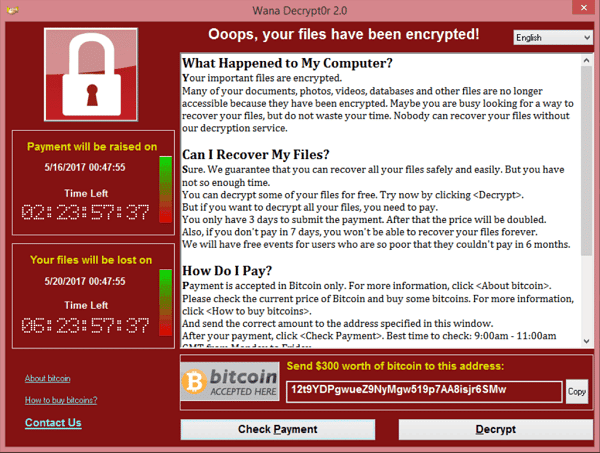
The WannaCry is the biggest ransomware attack in history. It affected hundreds of thousands of computer systems worldwide. Causing extensive damage to more than 200,000 computers across 150 countries.
This attack took place on May 12th, 2017. Exploited a security flaw in Microsoft Windows to encrypt data on infected computers and demand a ransom for the decryption key.
The WannaCrypt ransomware first looks for the kill switch domain name in the computer’s memory. If it isn’t there, the malware encrypts the computer data. Then attempts to exploit the SMB vulnerability to spread across random computers on the Internet and the local network.
WannaCry caused widespread panic and disruption. Many businesses and organizations were forced to shut down their systems to prevent the spread of the virus. Despite the efforts of security experts, the attack proved difficult to stop, resulting in 4 billion dollars in damages. On May 14th, Microsoft Security Researchers eventually discovered the vulnerability. They were able to create a patch to protect against future attacks. But the damage had already been done.
While WannaCry was eventually contained. It was a wake-up call for the need for better cybersecurity measures, and it remains the largest pay the ransom attack in history.
#2 NotPetya Ransomware Attack
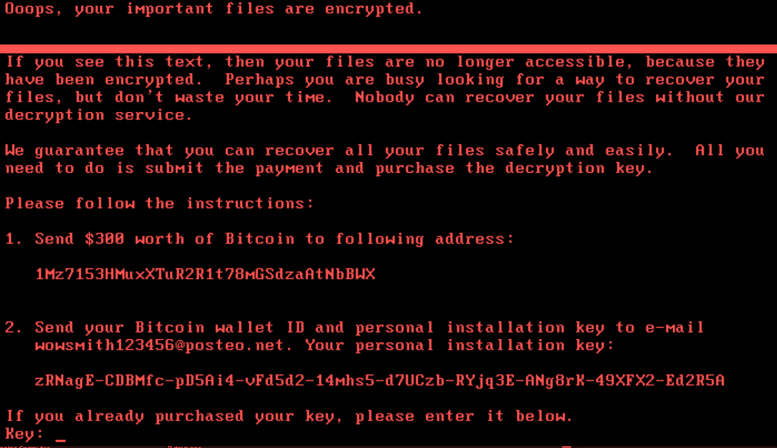
Petya was revived as GoldenEye, and The NotPetya variant came, resulting in a worldwide ransomware infection on June 27th, 2017. Affected computers primarily in Ukraine and Russia.
NotPetya is a type of ransomware that encrypts a computer’s hard drive and then pushes the ransom demand to the decryption key; it also contains a destructive payload that can delete important system files, making it impossible without the decryption to regain access.
The attack started with a phishing email that contained malicious ransomware encrypted as an attachment. Once opened, it would encrypt the hard drive and then display a fake check disk message followed by a ransom demand.
NotPetya ransomware spread with their custom tools, like Mimikatz, in an attempt to gather user credentials. These tools retrieve credentials from the lsass.exe process after being extracted. Credentials are then sent to PsExec or WMIC for distribution throughout the victims’ network utilizing system calls.
NotPetya quickly spread throughout Ukraine and Russia. Affecting government agencies, banks, energy companies, and even the Chernobyl nuclear power plant. The attack caused around 10 billion dollars in damage, and Maersk itself lost around 300 million. It was so destructive that some experts have called it a “wiper” rather than ransomware.
NotPetya also showed how destructive ransomware could be, as the payload made it impossible to recover data without the decryption key. This made it one of the most damaging ransomware attacks in history.
#3 SamSam Ransomware Attack
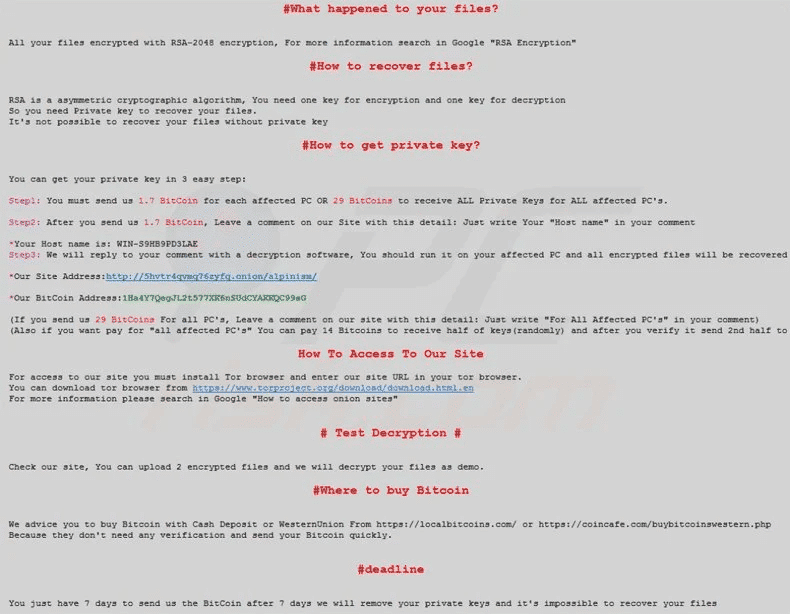
The SamSam ransomware was a cyberattack on January 6th, 2016. It affected many hospitals, businesses, and government agencies in the United States.
SamSam is ransomware encrypts data on an infected computer and then demands a ransom for the decryption key. The attack starts with a phishing email that contains malicious attachments. Once the attachment is opened, it will install the ransomware on the computer and start encrypting files.
The SamSam attackers would then manually log into systems using the remote desktop protocol (RDP) to deploy SamSam. Making it difficult for traditional antivirus software to detect and stop the attack.
Once they gained access. The SamSam ransomware group used hacking tools and public exploits to advance their privileges to a domain admin account. It was observed that the attacker took several days waiting for a domain administrator to log in.
The SamSam ransomware attack affected many hospitals in the United States. Causing them to cancel surgeries and appointments. The attack also caused significant damage to business and government agencies, exceeding 30 million dollars in damages.
Despite being one of the smaller ransomware attacks on this list, SamSam proved very destructive and costly. This shows that no organization is safe from a cyber attack, regardless of size.
#4 CryptoLocker Ransomware Attack
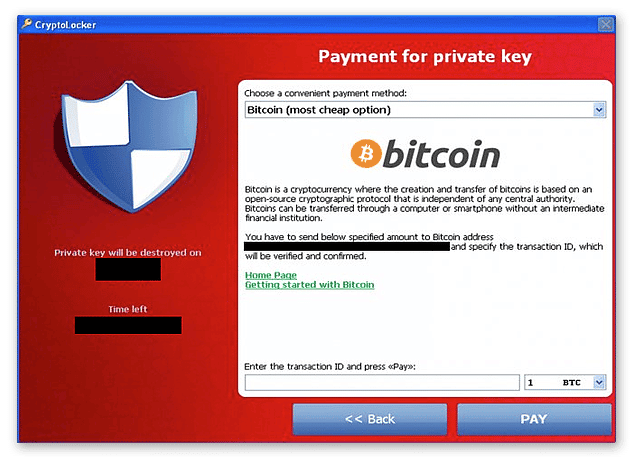
The CryptoLocker is one of the famous ransomware attacks that happened on September 5th, 2013, and affected computers worldwide.
Like any ransomware attack, This crypto-ransomware encrypted data on an infected computer and demanded a ransom for the decryption key. The attack started with a phishing email that contained a malicious trojan virus. Once any infected attachments were opened, it would install the ransomware on the computer and start encrypting files.
CryptoLocker was unique because it used asymmetric-key cryptography, a type of cryptography that uses two different keys, one public and one private. This made it very difficult to decrypt the encrypted files without the private key, which the attackers only held.
CryptoLocker quickly spread to thousands of computers. It was so successful that it spawned many copycat ransomware attacks. The attackers behind CryptoLocker made over 41,928 BTC which was $27 million(at that time) in ransom payments before the FBI shut down their operation.
While CryptoLocker was a very damaging ransomware attack. It also showed how effective ransomware could be at making money for the attackers. This is why we continue to see new ransomware variants being every year.
#5 Bad Rabbit Ransomware Attack
Bad Rabbit was a drive-by ransomware attack that took place on October 24th, 2017. This attack vector was a malicious dropper masqueraded as a fake Adobe Flash installation or update. Once the dropper was executed, it would encrypt the user’s files and demand a ransom of .05 BTC for decrypting the files.
This attack was particularly sophisticated in that it used multiple methods of propagating itself, including compromised websites and driver manipulation. As a result, this attack was able to spread quickly and cause significant damage. It followed a similar pattern to WannaCry and Petya/NotPetya in that it caused widespread havoc and disruption. The attackers used the EternalRomance exploit to gain initial access to victims’ systems. Then used the Mimikatz tool to harvest credentials from the Domain Controller. They also used tools designed to spread laterally within the same network, such as PsExec and WMI.
Bad Rabbit was a relatively small ransomware attack but one of the famous ransomware attacks as it managed to cause significant damage just by visiting a website. It showed that even smaller attacks could have a big impact.
It was one of the most damaging drive-by attacks regarding the amount of encrypted sensitive data. Kaspersky Lab first reported the attack, quickly spreading it to other security companies. Bad Rabbit is believed to be responsible for the largest ransomware attack in history. With over 200 targets got affected in Russia, Ukraine, Turkey, and Germany, causing significant transportation disruptions in various countries.
Lessons businesses can learn from these attacks.
These ransomware attacks caused billions of dollars in damage and disrupted businesses worldwide. While the private sector has been slow to respond to these threats, there are some lessons that businesses can learn from these attacks.
Now that you know some of the biggest ransomware families that attacked in recent history, here are some tips to help you protect yourself from ransomware.
Backup your data regularly!
It is one of the most important things you can do to protect yourself from ransomware. By having a critical data backup, you ensure that even if you encrypt files, you will still have a copy of them that can be used to restore your systems.
Patch your systems and software regularly!
By patching your systems, you can close the security weaknesses that attackers use to gain access to your systems. This is one of the most important things you can do to protect yourself from ransomware.
Educate your employees!
Teach your employees about the dangers of ransomware and how to avoid it. Ensure they know not to open email attachments from unknown senders or click on links in emails from unknown sources. Educate them to never use weak passwords.
Use a robust antivirus solution!
Make sure you have a robust antivirus solution to detect and block ransomware.
Future of Ransomware
Cyber Security is a rapidly evolving field, and ransomware is no exception.
In the past, ransomware was primarily a nuisance, encrypting files and demanding a small payment to decrypt them. But, recent years have seen a dramatic increase in both the frequency and severity of ransomware attacks. Today’s ransomware is more sophisticated than ever, and it is only getting more difficult to protect against. One of the biggest challenges posed by ransomware is the fact that it is constantly changing and evolving. Cybercriminals are always finding new ways to evade detection and infect devices. As a result, keeping pace with the latest threats is becoming increasingly difficult.
One possibility is that artificial intelligence and machine learning could be used to create more sophisticated ransomware that is better able to evade detection and encryption. Additionally, AI could target specific individuals or organizations with customized ransom demands. Another possibility is that ransomware will become more targeted and focused on causing as much damage as possible. This could include encrypting critical infrastructures such as hospitals or power plants.
Whatever the future holds, it is clear that the future of cyber security will need to adapt to meet the ever-changing threats posed by this damaging malware.




