RED TEAMING SERVICES
What is a Red Team Exercice?
Red teaming exercises are similar to penetration tests in terms of execution, as they replicate a real hacking scenario using the same techniques as hackers. However, red teaming assessment differs from pentesting, as it is a much deeper assessment specifically designed to replicate a skilled and persistent attacker attempting to breach your cybersecurity by any means necessary, without focusing on a specific technology. It provides a better perspective of an organization’s current cybersecurity posture, as it directly challenges the effectiveness of employees and systems to detect and respond to a real-world cyberattack.
Red Team vs Purple Team vs Blue Team

Red Team
- Penetration testing
- Social engineering
- Automated scanning
- Vulnerability exploitation

Purple Team
- Offensive and defensive
- Threat detection
- Collaborative security
- Security improvements

Blue Team
- Defensive security
- Gap analysis
- Forensics & threat hunting
- Incident response & SOC
Examples of Red Team Exercices
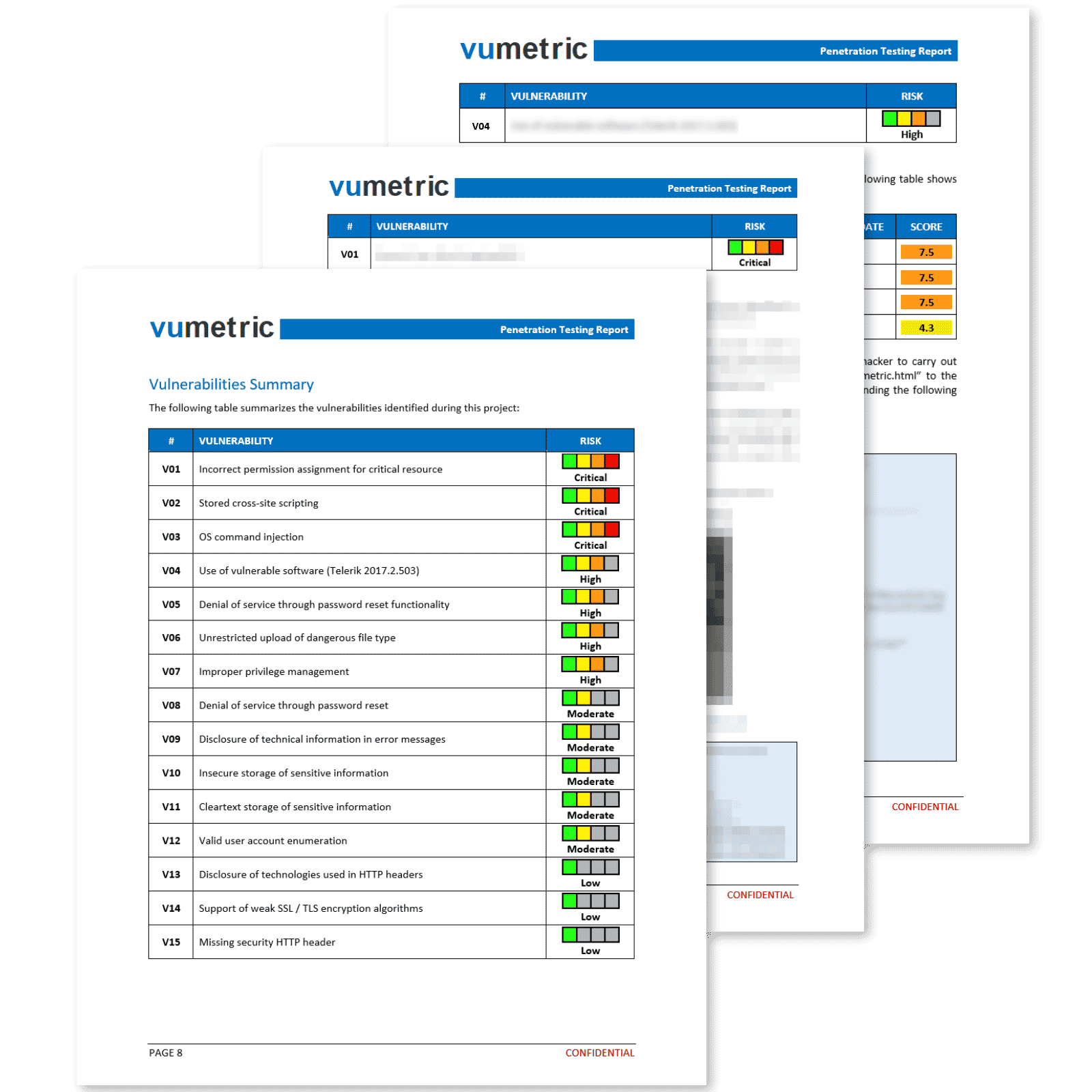
Generally aligned with an organization’s risk management strategy, red teaming assessment exercises must be tailored to a specific objective. This means that each red teaming engagement presents different parameters and targets, each adapted to the desired outcome. Here are examples of red teaming projects:
Attempting to gain the credentials of a specific IT administrator through phishing emails to further infiltrate the organization's technologies.
Gaining unauthenticated access into the Office 365 tenant to intercept communications and conduct Business Email Compromise (BEC) attacks.
Circumventing an internal network's detection systems to exfiltrate a mission-critical database.
Breaking out of an industrial network's segmentation to compromise smart production lines and cause denials of service.
Red Teaming vs Penetration Testing
| Penetration Testing | Red Teaming |
|---|---|
| Shorter time dedicated to testing | Extensive time dedicated to testing |
| Employees are informed of the test | Employees are generally not informed |
| Testers exploit known vulnerabilities | Testers seek to find and exploit new vulnerabilities |
| Testing scope is pre-defined | Scope is flexible and spans across various systems |
| Each system is tested independently | Systems are tested simultaneously |
Need Help To Assess And Improve Your Cybersecurity?
Protect Your Organization From Cyberattacks