What is a Ransomware Readiness Audit?
A ransomware readiness audit is an assessment designed to identify any opportunities for encrypting malware to infect an organization’s technologies and demand a ransom. Our ransomware testing services provide a real-world perspective of cyber risks that would enable ransomware to successfully encrypt your systems and lead to an incident.
Also, ransomware readiness testing is a process of simulating a ransomware attack on an organization in order to assess its ability to defend against and recover from such an attack. This type of testing can help organizations identify weaknesses in their security posture and make improvements to reduce the risk of a successful ransomware attack.
Our Ransomware Readiness Audit Services
By simulating the steps taken by a typical ransomware to encrypt as many systems as possible, our services help your organization determine the weakest systems that require further hardening to prevent infection.
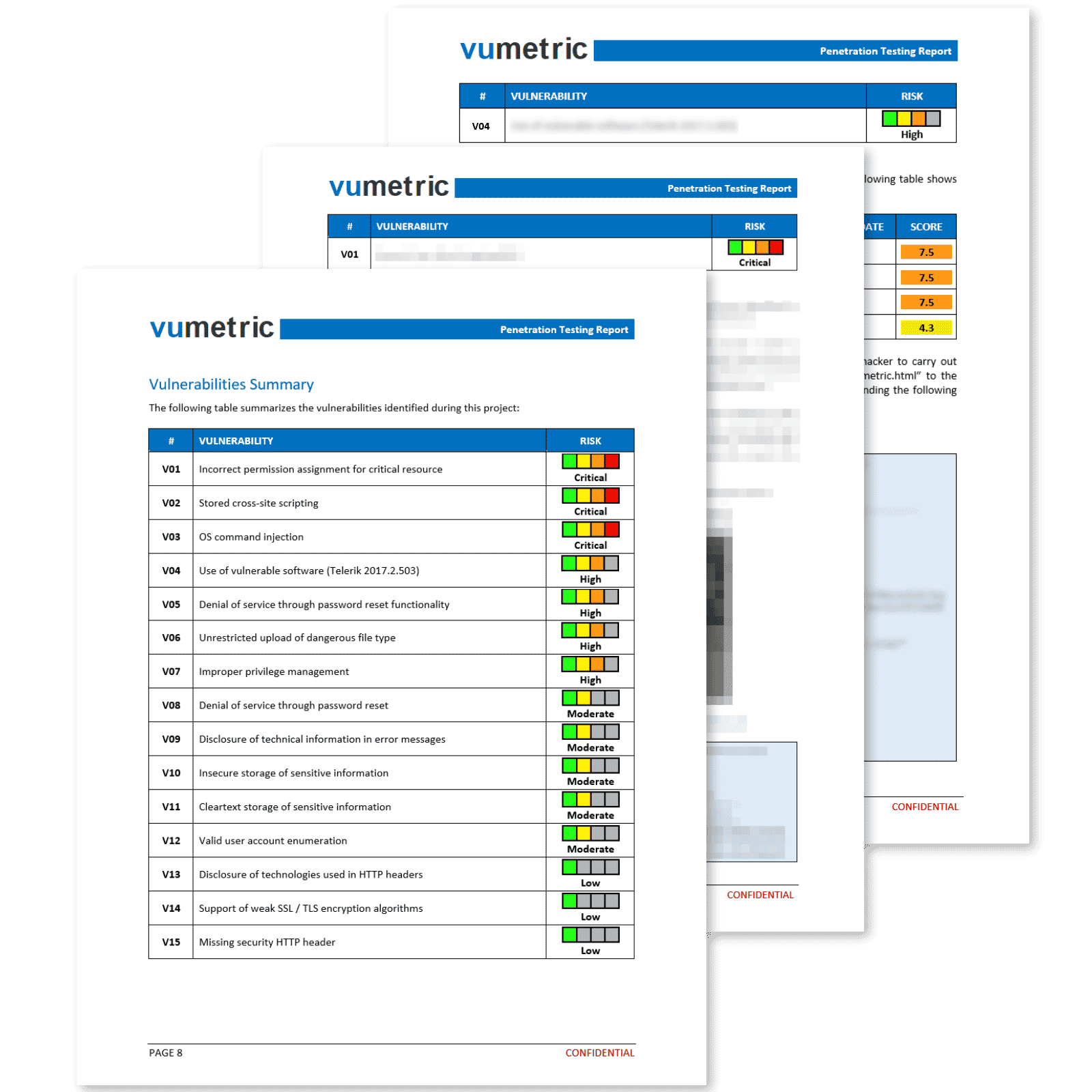
Our experts will analyze 12 key controls in your organization that would allow ransomware to successfully spread:
Firewall & Network
Configurations

User Activity Logging &
Audit Configurations

Employee Awareness
& Training

User Privileges &
Access Control
Network & Endpoint
Monitoring

Vulnerability & Patch
Management

Remote
Access

Email &
Web Security

Application
Whitelisting

Backup &
Restore

Incident
Response Plan

Third-Party
Vendor Management
Protect Your Organization Against Ransomware Attacks
While preventing ransomware entirely is impossible, various measures can be implemented to mitigate the most important risks. Being proactive remains the best defense against ransomware.
Provide the least user privileges possible
Remove inactive email addresses
Enforce strong password policies and multi-factor authentication
Perform frequent backups of any IT systems and segment backups
Whitelist only secure applications used by the organization
Better map your network configurations
The Importance of Ransomware Readiness Testing
- A ransomware readiness test can help you identify which systems and data are most at risk from a ransomware attack.
- The audit can also help you assess your current security posture and identify any gaps that could be exploited by attackers.
- The audit can provide recommendations on how to improve your ransomware readiness, such as by implementing better backup and recovery procedures.
- Finally, Ransomware readiness testing can provide numerous benefits to your organization, including improved security posture, reduced risk of a successful ransomware attack, and improved recovery capabilities. Additionally, this type of testing can also help organizations meet compliance requirements, such as those related to data security and incident response.
DID YOU KNOW?
“ With the emergence of ransomware-as-a-service (RaaS), ransomware attacks increased by 151% in 2021 ”